This is my tutorial on how to make a SonicWALL forward external DNS requests through a Pihole while keeping internal DNS working in an Active Directory environment.
This tutorial assumes that you have a Pihole set up and already filtering DNS for devices that have DNS manually set. For a tutorial on Pihole you can look here (link is not there yet.)
There are two NAT Polices that need to be made in the SonicWALL to forward DNS requests to the Pihole from devices. These devices can be on a separate VLAN as this should work for whatever source you specify.
The first rule is to allow DNS requests made from the Source address to actually reach the LAN and your Domain controller to that requests from other VLANS to your Domain Controller do not get redirected to the Pihole. If you don’t have this rule it breaks the internal DNS to other VLANS so make this policy first. The first policy is below:
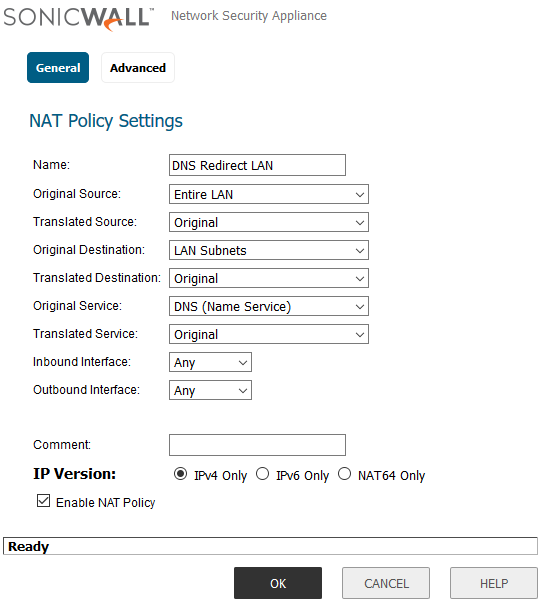
- Original Source are all the VLANS you want to be able to reach your LAN DNS.
- Translated source can be left alone but will be needed to redirect external DNS
- Original Destination should be where ever your DC DNS is located
- Translated Destination can remain Original
- Original Service needs to be DNS because we just want to affect DNS nothing else
- Translated Service can remain Original because we aren’t trying to say DNS is something else
- You also need to set the DC DNS resolver to the IP of the Pihole
The above rule will allow both the network that the DC is on and other VLANs making internal DNS requests to continue to function.
The next and final policy is one that will enable the sonicWALL to redirect External DNS requests to the Pihole mitigating users setting their own DNS in an attempt to bypass the Pihole. The policy is below:
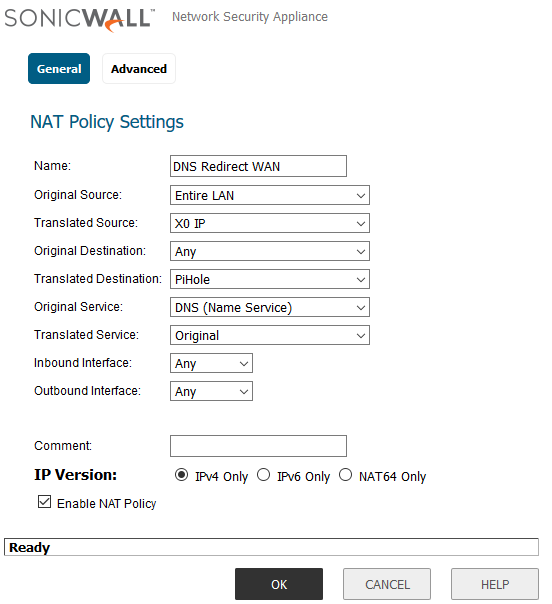
- Original Source are all the VLANS you want to be able to reach your LAN DNS.
- Translated source needs to be where your LAN gateway IP address is**
- Original Destination should be Any because we are redirecting Any external DNS request to the Pihole
- Translated Destination needs to be the Pihole because that’s what we are going to be redirecting requests to.
- Original Service needs to be DNS because we just want to affect DNS nothing else
- Translated Service can remain Original because we aren’t trying to say DNS is something else
** You need to set the Translated source to the IP address of the internal gateway that traffic is forwarded out of. This so that when users on the LAN attempt to make a DNS request using an external DNS provider they get a response from the gateway. If they didn’t get a response from the gateway they would receive a response from the Pihole but Windows would ignore it because the response is not from where Windows expects. **
Now if you make a nslookup request to doubleclick.net you get 0.0.0.0 as a response when using both Google and internal DNS but requests to google.com and twitter.com will work. You should also see requests filtering through your Pihole now.